#Data Encryption Hardware Market overview
Explore tagged Tumblr posts
Text
Data Encryption Hardware Market to Maintain Growth Momentum till 2037
The Data Encryption Hardware Market has experienced significant growth driven by escalating concerns around data security and privacy. Estimated at USD 1.73 billion in 2024, the market is poised to expand robustly, reaching an estimated USD 5.17 billion by 2037. This growth trajectory corresponds to a Compound Annual Growth Rate (CAGR) of approximately 8.3% during the forecast period from 2025 to 2037. The expanding digital ecosystem, increasing cyber threats, and stringent regulatory compliance worldwide underpin this accelerating demand for encryption hardware solutions.
Data Encryption Hardware Industry Demand
The Data Encryption Hardware Market encompasses physical devices designed to safeguard sensitive information by encrypting data, ensuring confidentiality, integrity, and authentication across digital communication and storage platforms. These hardware solutions provide an additional layer of security beyond software-based encryption by physically isolating cryptographic operations, thereby mitigating vulnerabilities to cyberattacks.
Demand for Data Encryption Hardware is primarily driven by several critical factors. First, these solutions offer cost-effectiveness by reducing potential financial losses from data breaches and non-compliance penalties. Second, they enable ease of administration, facilitating simplified key management and enhanced control over cryptographic processes. Additionally, many encryption hardware devices boast a long shelf life, supporting sustained security infrastructure investment with minimal maintenance requirements. Collectively, these benefits contribute to the rising adoption of encryption hardware across various industry verticals.
Request Sample@ https://www.researchnester.com/sample-request-7671
Data Encryption Hardware Market: Growth Catalysts and Primary Challenges
Key Growth Drivers:
Technological Advancements: The development of sophisticated cryptographic hardware such as Hardware Security Modules (HSMs) with enhanced processing power and integration capabilities fuels market growth. Innovations in miniaturization and power efficiency further boost adoption.
Outsourcing Trends: With organizations increasingly outsourcing IT and data security functions, reliance on robust hardware encryption solutions managed by third parties has risen. This trend stimulates demand for secure, reliable encryption hardware to safeguard outsourced data.
Regulatory Compliance and Data Privacy: Growing global regulatory mandates such as GDPR, HIPAA, and CCPA necessitate rigorous data protection practices. This compels organizations to invest in encryption hardware to comply with data security standards and avoid substantial penalties.
Market Restraint:
High Initial Investment: The relatively high upfront costs associated with deploying advanced encryption hardware may deter smaller enterprises or startups from immediate adoption, potentially limiting short-term market expansion.
Data Encryption Hardware Market: Segment Analysis
By Deployment Type:
Cloud-Based: This segment caters to organizations leveraging cloud infrastructures, requiring scalable encryption hardware solutions that can integrate with cloud platforms for secure data transmission and storage. Demand here is driven by the increasing migration to cloud environments and the need for remote, accessible security management.
On-Premise: Organizations with strict data sovereignty policies or legacy infrastructure tend to prefer on-premise deployment. This segment continues to hold steady demand due to the perceived control and security benefits it offers, particularly in highly regulated sectors.
By Product Type:
Hardware Security Modules (HSMs): HSMs lead the market as critical components providing secure key storage and cryptographic processing. Their robust security features and compliance alignment position them as preferred encryption devices.
Encryption Appliances: These devices offer dedicated encryption processing capabilities, often used in network security and data centers to ensure high-speed data protection.
Secure Storage Devices: Encrypted USB drives, external hard drives, and other storage devices secure sensitive data at rest, catering especially to mobile and field operations.
Trusted Platform Modules (TPMs): TPMs are embedded hardware chips used for device authentication and platform integrity, crucial for endpoint security.
Cryptographic Processors: These specialized processors accelerate cryptographic operations, supporting encryption in high-performance environments.
By End Use:
Banking & Financial Services: This sector drives substantial demand for encryption hardware, necessitated by the sensitive nature of financial transactions and regulatory mandates to safeguard customer data.
Government: Governments worldwide deploy encryption hardware extensively to protect classified information, secure communication channels, and uphold national security interests, significantly influencing market dynamics.
Data Encryption Hardware Market: Regional Insights
North America: North America remains a dominant market due to the presence of major cybersecurity firms and stringent data protection regulations. The region benefits from early adoption of cutting-edge encryption hardware solutions across industries, driven by heightened cyber threat awareness and substantial IT infrastructure investments.
Europe: Europe’s growth is fueled by strong regulatory frameworks such as GDPR and a growing emphasis on data sovereignty. Enterprises and public sector entities prioritize encryption hardware to meet compliance and protect consumer privacy, fostering steady market expansion.
Asia-Pacific (APAC): APAC is witnessing rapid growth due to increased digital transformation initiatives, expanding IT infrastructure, and rising cyberattacks. Governments and enterprises in emerging economies are investing heavily in encryption hardware to secure sensitive data and comply with evolving cybersecurity policies, positioning the region as a high-potential market.
Top Players in the Data Encryption Hardware Market
The Data Encryption Hardware Market is highly competitive, with several leading companies driving innovation and market expansion. Prominent players include Thales Group, IBM Corporation, Utimaco GmbH, Futurex, Entrust Corporation, Atalla, Securosys SA, Yubico AB, and others. These companies focus on delivering advanced encryption solutions with robust security features, fostering strategic partnerships, and expanding their global footprint to capture growing market demand.
Access Detailed Report@ https://www.researchnester.com/reports/data-encryption-hardware-market/7671
Contact for more Info:
AJ Daniel
Email: [email protected]
U.S. Phone: +1 646 586 9123
U.K. Phone: +44 203 608 5919
#Data Encryption Hardware Market#Data Encryption Hardware Market share#Data Encryption Hardware Market overview
0 notes
Text
Overcoming Challenges in Data Integration: Insights from Consulting Experts
Data integration for enterprises can take longer due to technological, financial, and time constraints. As a result, modifying data strategies to mitigate risks like incompatibility between many tools or budget overruns is crucial. Companies must also prepare for new compliance requirements to ensure ethical data operations. This post will explore such challenges in data integration while listing valuable insights from consulting experts in this domain.
What is Data Integration?
Data integration merges data from disparate origins and presents it to maximize comprehension, consolidation, and summarization effectiveness. Integrated data views rely on data ingestion, preparation, and advanced insight extraction. It also streamlines the data operations services across regulatory report creation, helpdesks, and 360-degree client life cycle management.
All data integration strategies involve the extract, transform, and load (ETL) pipelines regardless of business units or target industries. At the same time, the scope of planning and quality assurance in each process varies due to domain-specific data classification factors.
For instance, the accounting departments must handle extensive numerical data while interpreting legal and organizational requirements for transparency. On the other hand, production engineering and design professionals will use visualizations to improve goods or service packages. Accordingly, accountants will use unique tools distinct from engineers’ software.
Later, the leaders might want a comprehensive overview of the synergy between these departments. Therefore, they must determine efficient data integration strategies. The data will move between several programs, carrying forward many updates throughout a project’s progression based on those roadmaps.
Overcoming the Challenges in Data Integration Using Insights from Consulting Experts
1| Data Quality Hurdles
Linking, consolidating, and updating data from several sources will exponentially increase the quality-related threats. For instance, consider multimedia assets from social networks or unreliable news outlets. They can help your secondary market research and social listening initiatives. However, you want to verify the authenticity of gathered intelligence to avoid inaccurate data ingestion.
Evaluating relevance, freshness, and consistency is essential to data quality assurance from creation to archival. So, corporations have started leveraging data lifecycle management to boost dataset integrity, helping make integration less of a hassle.
Insights:
Most consulting experts suggest developing ecosystems that check and recheck quality metrics at each stage of a data integration lifecycle. Moreover, they recommend maintaining periodic data backups with robust version control mechanisms. Doing so will help quality preservation efforts if errors arise after a feature update or a malicious third party is likely to break the system using malware.
2| Networking and Computing Infrastructure Problems
Legacy hardware and software often introduce bottlenecks, hurting data integration’s efficiency. Modern integration strategies demand more capable IT infrastructure due to the breakthroughs like the internet of things (IoT), 5G networks, big data, and large language models. If a company fails to procure the necessary resources, it must postpone data integration.
Technologies integral to capturing, storing, checking, sorting, transferring, and encrypting data imply significant electricity consumption. Besides, a stable networking environment with adequate governance implementations enables secure data transactions. The underlying computing infrastructure is not immune to physical damage or downtime risks due to maintenance mishaps.
What Consulting Experts Say:
Enterprises must invest in reliable, scalable, and efficient hardware-software infrastructure. This will benefit them by providing a stable working environment and allowing employees to witness productivity improvements. Upgrading IT systems will also enhance cybersecurity, lowering the risk of zero-day vulnerabilities.
3| Data Availability Delays
Governments, global firms, educational institutions, hospitals, and import-export organizations have a vast network of regional offices. These offices must also interact with suppliers, contractors, and customers. Due to the scale of stakeholder engagement, reports concerning office-level performance and inventory might arrive late.
Underproductive employees, tech troubleshooting, slow internet connectivity, and a poor data compression ratio will make data sourcing, updating, and analyzing inefficient. As a result, a data integration officer must address time-consuming activities through strategic resource allocation. If left unaddressed, delays in data delivery will adversely affect conflict resolution and customer service.
Expert Insights:
Train your employees to maximize their potential and reduce data acquisition, categorization, and transformation delays. Additionally, you will want to embrace automation through artificial intelligence (AI) applications. Find methods to increase the data compression ratio and accelerate encryption-decryption processing cycles. These measures will help accomplish near-real-time data integration objectives.
4| Vendor Lock-ins
A vendor lock-in results from inconvenience and restrictions when a client wants to switch to another service provider or toolkit. Although data integration platforms claim they celebrate the ease of migrating databases with competitors, they might covertly create vendor lock-ins.
For instance, some data sourcing and sorting ecosystems might limit the supported formats for bulk export commands. Others will use misleading methods to design the graphical user interface (GUI) of account deletion and data export features. They involve too many alerts or generate corrupt export files.
Practical Insights:
Combining multiple proprietary and open-source software tools offers the best cost optimization opportunities. When you select a data vendor, audit the tools the willing data integration providers use to deliver their assistance. Do they use a completely proprietary system based on an unknown file format unsupported by other platforms?
Finally, you must check all the data import, export, and bulk transfer options in vendors’ documentation. After you check a data firm’s current client base, track its online ratings and scan for red flags indicating potential vendor lock-ins.
5| Data-Related Ethical and Legal Liabilities
Confidentiality of investor communication and stakeholders’ privacy rights are two components of legal risk exposure due to enterprise data integration. Additionally, brands must interpret industry guidelines and regional directives for regulatory disclosures.
They must comply with laws concerning personally identifiable information (PII) about employees and customers. Otherwise, they will attract policymakers’ ire, and customers will lose faith in brands that do not comply with the laws of their countries.
Insights:
Consulting experts recommend collaborating with regional legal teams and global governance compliance specialists. After all, mitigating legal risks can help increase business resilience.
Improved compliance ratings have also benefited several brands wanting to be attractive to impact investors. Meanwhile, customers demanding ethical data operations at business establishments love supporting brands with an exceptional governance culture.
Conclusion
Most brands need specialists' help to develop consolidated data views during reporting because they have flawed data integration strategies. So, they require trustworthy insights from reputed consulting experts with a proven track record of overcoming challenges in data integration. The selected data partners must excel at ETL implementation, governance compliance, and data quality management (DQM).
The corporate world champions data-centric business development. Understandably, the need for scalable data integration reflects the increased stakeholder awareness regarding the importance of connecting disparate data sources. With transparent, fast, and accurate data, organizations will enhance their competitive edge amid this intense digital transformation race.
3 notes
·
View notes
Text
BPO Software Solutions: Industry Overview and Key Trends for 2025
The BPO industry acts like a giant engine, boosting how efficiently businesses work and sparking new ideas all over the world. So, what keeps it humming? Increasingly, the answer is innovative BPO software solutions. These aren't simple contact center software solution tools; they streamline entire processes, manage complex jobs, and ensure customers have fantastic experiences.
What Are BPO Software Solutions, Anyway?

Simply put, BPO software solutions are digital tools designed to handle and improve various outsourced business operations. This includes a wide range of activities, from customer support and telemarketing to data management, human resources, and even financial tasks. These systems really form the core infrastructure that lets BPO firms do their work well and smoothly. Without strong software, a BPO operation would quickly fall into disarray! These are complex systems, not just simple programs, and they manage a vast array of jobs. They typically include:
Phone system managers: The software that powers your phone lines and call routing.
Client relationship software: Your central place for all customer information & history.
Workforce organizers: Tools that help you plan who does what and when.
Analytics views: Visual summaries of how things are performing.
Process automation kits: Digital assistants that take over routine steps.
Service quality checkers: Features designed to uphold excellent service.
Knowledge bases: Digital libraries where all your essential information lives.
The Essential Role of BPO Technology in Today's Market
Have you ever wondered how a call center handles thousands of customer queries daily, across different time zones? You could say smart BPO software solutions make things happen. These systems take over routine jobs, put customer information right at agents' fingertips, and ensure everyone communicates without a hitch. They're the unseen force behind pleasant customer calls and seamless back-office tasks.
Gives you important insights from all the collected data.
Makes it easy for teams to work from anywhere.
Key Trends Shaping BPO Software Solutions for 2025
The BPO world constantly adapts to new technologies and customer demands. Here are some of the major trends driving the evolution of BPO software solutions as we head into 2025:
AI and Automation in BPO Operations
Artificial Intelligence (AI) isn't just a buzzword anymore; it's transforming BPO software solutions. This way, your talented people can focus on tasks that truly need their empathy, problem-solving skills, and smart thinking.
Cloud-Based BPO Software Solutions
The shift to cloud computing is undeniable. These Cloud-based Telephony software solutions offer incredible flexibility, scalability, and cost-effectiveness. Forget shelling out big bucks for hardware! Today's BPO providers simply access strong software online, paying only for what they actually use. This setup lets them quickly grow or shrink their services based on client needs, which is perfect for the fast-changing BPO world. Plus, it makes working from anywhere a breeze – a big deal in our current global economy. If your BPO tech feels old-fashioned, cloud-based options are clearly the way forward.
Customer Experience with Integrated Software
The ultimate goal of many BPO services is to deliver an outstanding customer experience. Also, expect much smarter connections with CRM systems inside this software. This gives agents instant access to past conversations and preferences, helping them offer service that's both personal and fast.
Data Security and Compliance
In an era of increasing cyber threats and strict data privacy regulations (like GDPR or CCPA), data security is paramount for BPO software solutions. BPO companies manage a lot of private customer information, so they absolutely need strong security and proper certifications. Soon, their software will offer even tougher encryption, multiple ways to log in, and detailed and secure call records of everything that happens, all to keep data safe and follow the rules. In the BPO business, earning trust is huge, and reliable software helps build that.
Why KingAsterisk Understands Your BPO Software Needs
At KingAsterisk, we deeply understand the critical role BPO software solutions play in a call center's success. As a dedicated provider of call center solution services, we consistently develop and implement the kind of robust, future-ready software that empowers BPO operations. We bring deep knowledge from many different areas. This means if you need a strong dialing system, smart call routing, or detailed reports, we'll build a solution that fits your exact needs.
We actively incorporate these evolving trends into our offerings, ensuring that our clients remain at the forefront of the industry. For example, our systems bring in top-notch analytics that actually show you what's happening with your operations, giving you clear insights. We also make sure everything is super easy to use, so your agents can spend their time helping customers instead of wrestling with tricky software.
Conclusion
The world of BPO software solutions keeps changing and holds a lot of promise. Businesses that embrace big shifts – like AI, automation, cloud tech, and stronger security – can make sure their operations are ready for the future and give clients awesome service. Teaming up with a company that really gets these details, just like KingAsterisk, offers a real edge over competitors. Are you set to get your BPO operations in top shape for 2025 and beyond?
0 notes
Text
How GCP Confidential Computing develops trusted AI

How Confidential Computing Builds Trusted AI
GCP Confidential Computing changed enterprise cloud-based sensitive workload management. Google's hardware ecosystem development makes Confidential Computing compatible with privacy-preserving AI and multi-party data analytics, boosting adoption.
Google Cloud unveils its latest Confidential Computing advancements, illustrating how clients protect their most sensitive workloads, including AI.
Newest innovations
A glance at GKE Nodes and private virtual machines with NVIDIA H100 GPUs for AI applications.
A private Vertex AI Workbench preview
An overview of Confidential Space using the widely available NVIDIA H100 and Intel TDX GPUs.
General access, secret GKE Nodes on C3 systems with integrated acceleration and Intel TDX.
On AMD SEV-SNP N2D computers, confidential GKE nodes are available.
Private AMD SEV virtual machines on C4D machines preview
Speed up your Confidential Compute trip with Gemini Cloud Assist's preview.
Confidential Computing New Applications
Businesses using GCP Confidential Computing to unlock commercial breakthroughs affect all major industries.
AiGenomix
AiGenomix uses Google Cloud Confidential Computing to provide unique infectious disease surveillance, early cancer detection, and pharmaceuticals intelligence with a global network of public and private partners.
Google Ads
Google Ads uses confidential matching to link first-party customer data for marketing. Google Ads products are the first to employ confidential computing, and additional companies will follow suit.
Swift
Swift is using GCP Confidential Computing to power a money laundering detection model while protecting the privacy of some of the biggest banks.
Confidential Computing
Confidential VMs, GKE, Dataflow, Dataproc, and Space safeguard data in use.
Encrypt data during processing.
A simple, user-friendly implementation does not sacrifice performance.
Confident collaboration with data ownership
Benefits
A secrecy breakthrough
Confidential Virtual Machines, a breakthrough technology, lets customers secure their cloud data during processing.
Simply understood by all
Google Cloud lets users encrypt data in-app without changing app code or affecting speed.
Creating new possibilities
Confidential Computing opens new doors. Companies can collaborate while protecting data.
GCP Confidential Computing
Secret Computing Platform
Secret VMs
Cloud data can be protected by confidential virtual machines (VMs) encrypting data-in-use during processing. Modern AMD, Intel, and other CPUs have security protections for secret virtual machines. With GCP Confidential Computing, customers can trust their cloud data to remain private.
Google Cloud uses the Intel AMX CPU accelerator on the general-purpose C3 machine class for Confidential VMs for AI/ML applications. Confidential VMs on the C3 machine series secure AI data and models at the hardware level and boost deep learning and inference performance.
Confidential H100 GPU VMs
Companies can use AI and machine learning while securing sensitive data using accelerator-optimized A3 machine series with NVIDIA H100 GPUs' confidential virtual machines (VMs). With H100 GPUs, confidential virtual machines (VMs) protect data from GPU entry to output. This reduces the risk of privileged users or malicious actors gaining unauthorised access. Confidential VMs on the A3 machine line provide a trusted execution environment for AI applications, enabling businesses to collaborate more freely and securely.
Secret GKE Nodes
Confidential GKE Nodes encrypt GKE cluster data while retaining performance. The same technology powers Confidential GKE Nodes and VMs. This functionality lets you encrypt memory with processor-created, node-specific keys. Since the keys are produced in hardware during node formation and only live in the CPU, Google and other host nodes cannot access them.
Private Area
Confidentiality Space protects sensitive data while allowing businesses to aggregate and analyse it. Organisations can perform collaborative data analysis and machine learning (ML) model training with data security from all parties, including cloud service provider access. Confidential Space integration with Privacy Sandbox provides a trusted execution environment for privacy-preserving ad campaign analytics and retargeting post-cookie.
Secret Dataflow and Dataproc
Fully controlled Dataflow supports several machine learning and streaming analytics use cases at scale. Dataflow supports Compute Engine Confidential VMs, which allow inline memory encryption, for data pipelines.
Dataproc manages Spark, Hadoop, and other open source technologies and frameworks for huge data processing. Confidential Dataproc lets you secure inline memory using Compute Engine Confidential virtual machines. This improves security, especially for sensitive data.
All features
Using real-time encryption
Google Cloud users can encrypt data while using cloud services for hidden computing and AMD, Intel, and other CPU security capabilities. Customers may trust that their data will be encrypted while processing.
Elevate and move privately
Google Cloud wants to simplify GCP Confidential Computing. All your workloads—new and old—can run as Confidential VMs, making the transfer easy. You don't need to change app code to use Confidential VMs. Simple as checking one box.
Detecting sophisticated persistent assaults
GCP Confidential Computing enhances Shielded virtual machine rootkit and bootkit protection. This simplifies ensuring the integrity of your private virtual machine's operating system.
Enhanced creativity
GCP Confidential Computing could enable impossible computing scenarios. Cloud-based enterprises can now collaborate on critical data in secrecy.
Great performance
Regular N2D virtual machines function like confidential ones.
GCP Private Computing Cost
Confidential VM costs depend on machine kinds, persistent discs, and other resources.
#GCPConfidentialComputing#ConfidentialComputing#GoogleAds#virtualmachines#ConfidentialGKENodes#ConfidentialSpace#technology#technews#technologynews#news#govindhtech
0 notes
Text
Thin Clients: Powering the Future of Virtual Workspaces

According to a comprehensive new market research report, the global thin client market was valued at USD 1.4 billion in 2022 and is projected to expand at a healthy compound annual growth rate (CAGR) of 4.2% from 2023 to 2031, reaching USD 2.1 billion by the end of 2031.
Market Overview Thin clients are minimalist computing terminals that rely on a centralized server or cloud infrastructure to execute applications, process data, and store information. In contrast to traditional PCs, thin clients minimize local processing power and storage, offering organizations a secure, scalable, and cost-effective alternative for deploying desktop virtualization solutions. Their deployment spans virtual desktop infrastructure (VDI), call centers, remote work environments, educational institutions, healthcare facilities, and financial services, where centralized management, standardized configurations, and data security are paramount.
Market Drivers & Trends Two primary forces are fueling thin client market growth:
Adoption of Cloud Computing: Enterprises are increasingly migrating to cloud-based platforms for email, storage, office software, and vertical-specific applications. Cloud-based VDI enables thin clients to access virtual desktops and applications on demand, delivering flexibility, rapid deployment, and operational efficiency. According to the European Commission, 42.5% of EU enterprises purchased cloud computing services in 2023, driving demand for thin client endpoints.
Demand for Centralized Management: Organizations seek comprehensive solutions for security management, patch deployment, asset tracking, and configuration control. Thin client architectures streamline these processes through a single pane of glass, reducing IT overhead and ensuring compliance with corporate policies.
Additional trends include:
Miniaturization and All-in-One Designs: Manufacturers are introducing compact, fanless thin profiles and all-in-one units to conserve space in modern offices.
Enhanced Security Features: Secure boot, multi-factor authentication, and hardware-based encryption are becoming standard to protect sensitive data in enterprise and government deployments.
Sustainability Initiatives: Energy-efficient hardware and reduced e-waste are driving preference for thin clients in organizations committed to green IT.
Latest Market Trends
Virtual Desktop Infrastructure (VDI) Acceleration: The shift toward hybrid and remote work models has reignited interest in VDI, with enterprises leveraging thin clients to deliver secure, high-performance virtual desktops to distributed workforces.
AI and Edge Computing Integration: Vendors are exploring AI-accelerated thin clients that offload inference workloads to edge servers, improving responsiveness for video analytics, telemedicine, and industrial automation.
Subscription-Based Models: Thin clients are increasingly offered as part of Device-as-a-Service (DaaS) and Desktop-as-a-Service (DaaS) bundles, simplifying procurement and enabling predictable OPEX budgeting.
Key Players and Industry Leaders The thin client arena is characterized by a mix of established IT hardware vendors and specialized endpoint solution providers. Leading players profiled in the market report include:
10ZiG
Acer Inc.
Advantech Co., Ltd.
Cisco Systems, Inc.
Dell Inc.
HP Development Company, L.P.
IGEL
NComputing Co. LTD
Praim SRL
Samsung
Each company is analyzed across parameters such as product portfolio, geographic footprint, recent product launches, strategic alliances, and financial performance.
Recent Developments
March 2023: Stratodesk announced certification of LG Business Solutions thin clients with NoTouch OS, enabling seamless deployment across private and public clouds, and giving IT teams enhanced flexibility for endpoint management.
August 2022: 10ZiG unveiled the 7500q thin client series featuring Intel quad-core processors, a 15.6-inch FHD display, up to 8 GB DDR4 RAM, multiple USB and HDMI interfaces, and up to 10 hours of battery life for mobile applications.
Access an overview of significant conclusions from our Report in this sample - https://www.transparencymarketresearch.com/sample/sample.php?flag=S&rep_id=40028
Market Opportunities and Challenges
Opportunities:
Emerging Economies: Rapid digital transformation in the Asia Pacific, Latin America, and Middle East & Africa presents substantial growth prospects for thin client adoption in sectors like education, public administration, and healthcare.
IoT Convergence: The proliferation of IoT endpoints creates demand for secure, manageable gateways, positioning thin clients as ideal enablers for smart manufacturing and logistics solutions.
Challenges:
Legacy Infrastructure Barriers: Organizations with entrenched PC deployments may resist migration to thin client architectures due to perceived risk and migration costs.
Network Dependence: Thin clients require reliable, high-bandwidth connectivity; inadequate network infrastructure in remote or underdeveloped regions can hamper deployment.
Future Outlook The thin client market is poised for steady growth through 2031, driven by digital workplace initiatives, sustainability mandates, and the need for resilient endpoint security. Innovations in edge computing, zero-trust security models, and AI-driven management tools will further enhance thin client value propositions.
Analyst Viewpoint "The convergence of cloud computing and the rising importance of data security in hybrid work environments underscore the strategic relevance of thin clients. Vendors that invest in advanced virtualization protocols, AI-based endpoint management, and energy-efficient designs are best positioned to capture market share over the next decade," says the lead analyst for enterprise infrastructure.
Market Segmentation
The report segments the thin client market as follows:
Component:
Hardware
Services
Deployment Mode:
Desktop-based
Mobile-based
Enterprise Size:
Small and Medium Enterprises (SMEs)
Large Enterprises
End-Use Vertical:
Banking, Financial Services and Insurance (BFSI)
Healthcare
Retail
Manufacturing
Government
IT & Telecom
Education
Transportation & Logistics
Others (Oil & Gas)
Regional Insights
North America accounted for the largest market share in 2022, driven by rapid adoption of cloud-based solutions, advanced IT infrastructures, and strong presence of key vendors. Europe follows closely, supported by digital transformation agendas in the UK, Germany, and France. The Asia Pacific is expected to register the highest CAGR from 2023 to 2031, fueled by industrial automation in China, government initiatives in India, and technology investments in Southeast Asia.
Why Buy This Report?
Gain data-driven insights on market size, forecast, and growth rate (CAGR 2023–2031).
Evaluate competitive landscape with detailed profiles of leading players.
Understand the impact of cloud migration, VDI acceleration, and security trends.
Identify emerging opportunities in new regions and verticals.
Leverage strategic recommendations from expert analysts to inform investment decisions.
About Transparency Market Research Transparency Market Research, a global market research company registered at Wilmington, Delaware, United States, provides custom research and consulting services. Our exclusive blend of quantitative forecasting and trends analysis provides forward-looking insights for thousands of decision makers. Our experienced team of Analysts, Researchers, and Consultants use proprietary data sources and various tools & techniques to gather and analyses information. Our data repository is continuously updated and revised by a team of research experts, so that it always reflects the latest trends and information. With a broad research and analysis capability, Transparency Market Research employs rigorous primary and secondary research techniques in developing distinctive data sets and research material for business reports. Contact: Transparency Market Research Inc. CORPORATE HEADQUARTER DOWNTOWN, 1000 N. West Street, Suite 1200, Wilmington, Delaware 19801 USA Tel: +1-518-618-1030 USA - Canada Toll Free: 866-552-3453 Website: https://www.transparencymarketresearch.com Email: [email protected]
0 notes
Text
Nautilus Hyosung Halo ATM
Introduction
ATM technology has come a long way since those basic machines that just spit out cash. Today, banking customers want more—quick, secure, and easy-to-use machines that fit their busy lifestyles. Nautilus Hyosung’s Halo ATM OceanATM stands out by offering innovative features. It transforms how banks serve customers and helps financial institutions operate more smoothly. Choosing the right ATM technology isn’t just about replacing old machines. It’s about making banking better, safer, and more accessible for everyone.
Overview of Nautilus Hyosung Halo ATM OceanATM
What is the Nautilus Hyosung Halo ATM OceanATM?
The Nautilus Hyosung Halo ATM OceanATM is a versatile self-service machine built to handle a wide range of banking tasks. Its sleek design blends modern looks with tough durability. It’s part of Nautilus Hyosung’s smart lineup of ATMs, focused on delivering secure and reliable service.
Key Features and Innovations
This ATM introduces several tech perks. It offers fast, secure transactions with advanced fraud prevention. The OceanATM can support deposits, cash withdrawals, bill payments, and even mobile top-ups. Its touch screen, multilingual options, and accessibility features make it easy for anyone to use. Connectivity is a key feature too — it stays linked with bank networks in real time.
Market Position and Adoption
Many banks worldwide now turn to OceanATM for its reliability and rich features. Adoption rates are climbing fast, especially in regions needing easy access to banking. Its ability to compete with other high-tech ATMs makes it a top choice for financial firms aiming to stand out.
Technical Specifications and Functionality
Hardware and Design
The OceanATM features sturdy hardware built to last in various environments — from busy city centers to rural areas. Its ergonomic design makes transactions fast and simple, with clear screens and easy-to-reach components. It’s designed to resist weather and tampering.
Software and Security
All functions run on secure software with layers of user authentication, like PINs or biometric scans. Data encryption keeps customer info safe during transactions. Certified to meet strict security standards like PCI DSS, it offers peace of mind for both banks and users.
Transaction Capabilities
OceanATM can do much more than cash withdrawals. It supports deposits, bill payments, fund transfers, and digital wallet integration. Customers can use mobile apps or contactless payment options for extra convenience.
Benefits for Financial Institutions and Customers
Enhanced User Experience
Customers find the OceanATM easy to use, thanks to its simple interface and multilingual support. Accessibility options such as voice guidance or larger screens help meet diverse needs. Many users report faster, more pleasant transactions.
Operational Efficiency
Self-service features mean banks need fewer staff at counters. The machine handles many routine tasks, freeing employees for more complex services. Maintenance is simplified with remote diagnostics, reducing downtime.
Security and Compliance
Built with anti-fraud tools, OceanATM detects suspicious activity in real time. Its secure design helps banks meet all regulatory standards, shielding transactions from hacking or fraud attempts.
Cost Savings and ROI
Since it reduces staffing needs and minimizes maintenance costs, OceanATM offers good value. Banks can deploy fewer machines and still support more customers. Many are seeing faster returns on their investment.
Deployment Scenarios and Real-World Applications
Retail Banking Branches
Adding OceanATM speeds up customer visits in branches. Customers can quickly complete deposits and withdrawals, reducing wait times and improving overall service.
Remote and Rural Areas
In neighborhoods without many bank branches, OceanATM makes banking accessible. It provides essential services where traditional bank staff might not be available.
Convenience Stores and Non-Bank Venues
These machines fit well in retail and utility locations. Customers can withdraw cash or pay bills during shopping trips or errands, expanding banking reach.
Examples of Successful Implementations
Some banks report decreased wait times and higher customer satisfaction after installing OceanATM. In a rural region, deployment increased banking access by 30%, proving its effectiveness beyond cities.
Maintenance, Support, and Future Developments
Maintenance and Support Infrastructure
Remote diagnostics and scheduled updates keep OceanATM running smoothly. Support teams can identify issues early and fix them promptly, lowering downtime.
Upgrades and Scalability
The system easily adapts to new features. As banking needs grow, the OceanATM can be upgraded with the latest software or hardware modules, ensuring it stays relevant.
Future Trends in ATM Technology
Expect to see more AI features, biometric security like fingerprint or face scans, and better IoT connectivity. These tools will make ATMs smarter, safer, and more personalized.
Conclusion
The Nautilus Hyosung Halo ATM OceanATM offers a powerful blend of security, functionality, and user-friendliness. It helps banks serve customers faster, safer, and more comfortably. Its resilient design and advanced features make it a smart choice for any institution looking to upgrade their self-service offerings. For banks ready to lead the way, OceanATM provides a clear path toward digital growth and better customer experiences. Explore how OceanATM can fit into your branch or community today.
0 notes
Text
Edge Computing Market Resilience and Risk Factors Impacting Growth to 2033
Introduction
Edge computing is rapidly transforming the digital landscape by bringing data processing closer to the source of data generation. Unlike traditional cloud computing, which relies on centralized data centers, edge computing enables real-time data analysis and reduced latency by processing data at the network's edge. This technology is becoming increasingly critical with the rise of Internet of Things (IoT) devices, autonomous vehicles, and real-time analytics. The edge computing market is poised for substantial growth, driven by advancements in 5G technology, increased demand for low-latency applications, and the growing adoption of IoT devices.
Market Overview
The global edge computing market is experiencing robust growth. According to industry reports, the market size was valued at approximately USD 10 billion in 2022 and is expected to reach over USD 60 billion by 2032, growing at a compound annual growth rate (CAGR) of around 20%. The market encompasses hardware, software, and services that facilitate edge data processing and analytics. Key industry players include tech giants such as Amazon Web Services (AWS), Microsoft Azure, Google Cloud, and edge-specific firms like EdgeConneX and Vapor IO.
𝗗𝗼𝘄𝗻𝗹𝗼𝗮𝗱 𝗮 𝗙𝗿𝗲𝗲 𝗦𝗮𝗺𝗽𝗹𝗲 𝗥𝗲𝗽𝗼𝗿𝘁👉https://tinyurl.com/4u5uvp8e
Key Market Drivers
Proliferation of IoT Devices: With billions of connected devices generating vast amounts of data, edge computing offers a solution to handle data locally, reducing bandwidth usage and enhancing response times.
Need for Low Latency: Industries such as autonomous vehicles, healthcare, and gaming require real-time data processing, which edge computing can efficiently provide.
Advancements in 5G Technology: The rollout of 5G networks is a significant enabler for edge computing, offering faster and more reliable connectivity.
Data Privacy and Security: By processing data closer to its source, edge computing enhances data security and compliance, particularly for industries dealing with sensitive information.
Increasing Demand for Smart Applications: The growing use of smart applications in smart cities, industrial automation, and augmented reality (AR) drives the adoption of edge computing.
Industry Trends
1. Hybrid Edge-Cloud Models
Many enterprises are adopting hybrid models that combine edge computing with cloud computing to leverage the best of both technologies. This approach allows critical data to be processed at the edge while less time-sensitive data is sent to the cloud for further analysis.
2. Edge AI (Artificial Intelligence)
Integrating AI at the edge enables devices to make autonomous decisions without the need for cloud-based processing. This trend is particularly beneficial in areas like predictive maintenance and personalized customer experiences.
3. Enhanced Edge Security Solutions
As edge devices are often more vulnerable to cyberattacks, there is a rising demand for robust security solutions. Companies are increasingly investing in edge-specific cybersecurity measures, including encryption, threat detection, and secure access controls.
4. Micro Data Centers
The deployment of micro data centers at the edge is gaining momentum. These small-scale data centers provide localized processing and storage, contributing to faster data processing and improved reliability.
Market Segmentation
1. By Component
Hardware
Software
Services
2. By Application
Industrial IoT
Smart Cities
Healthcare
Retail
Autonomous Vehicles
Gaming
3. By Industry Vertical
Manufacturing
Transportation
Healthcare
Energy & Utilities
Telecommunications
Regional Analysis
The North American region holds the largest share of the edge computing market due to early technology adoption, strong infrastructure, and the presence of key industry players. Europe follows closely, with increasing investments in smart cities and industrial automation. The Asia-Pacific region is expected to exhibit the highest growth rate, driven by advancements in telecommunications and increasing adoption of IoT devices.
Challenges and Opportunities
Challenges:
High initial setup costs
Limited scalability compared to cloud computing
Management complexities of distributed networks
Opportunities:
Expansion of 5G networks
Growth of edge-enabled AI applications
Increasing demand for real-time analytics
Future Outlook
The future of the edge computing market looks promising, with significant potential in sectors such as healthcare, automotive, and industrial IoT. As edge computing technology matures, it is expected to play a critical role in emerging technologies such as the metaverse and Industry 4.0.
Conclusion
Edge computing is reshaping how data is processed and analyzed, offering significant advantages in terms of speed, efficiency, and security. With its rapid adoption across various industries, the edge computing market is set to witness remarkable growth in the coming decade. As businesses and technology providers continue to innovate, edge computing will remain at the forefront of digital transformation strategies, driving advancements in smart applications, real-time analytics, and data-driven decision-making.
Read Full Report:-https://www.uniprismmarketresearch.com/verticals/information-communication-technology/edge-computing
0 notes
Text
Cloud based CRM Software
Why it is Necessary Cloud-Based CRM Introduction
In today's fast-paced business environment, maintaining strong customer relationships is perhaps the most important condition for growth and success. Because of that, Cloud-Based CRM Software has come to be very important for businesses in managing customer data and improving customer communications and sales performance. Unlike traditional CRM solutions, cloud-based platforms are flexible and scalable and allow modern businesses to reach their customers from anywhere. This article provides an overview of the main benefits, functionalities, and best solutions in the marketplace.
What is Cloud-Based CRM Software?
Cloud-based CRM software is defined as an offsite network-based customer relationship management system. Through the Internet, businesses may log into any of these tools to store their customers' information safely on their hosted cloud rather than on their local servers, which would require extensive resources for a well-designed hardware infrastructure for storing data along with high IT maintenance costs.
Most Valuable Features in Cloud-Based CRM Software
Centralized Data Management: Every piece of customer-related information, including contacts, communiqués, and transaction details, is saved securely under one roof.
Automation Tools: For example, they could follow up on emails that should be sent out, campaigns automatically launched for lead scoring, or full data entry for the incoming leads.
Analytics and Reporting: It's real-time information on the sales performance, the behavior of customers, and even the trends of marketing.
Integration Capabilities: Seamless integration with third-party applications for email marketing, social networks, or e-commerce solutions.
Accessibility: Any type of device with internet connectivity can access the system because it makes remote work capabilities much more powerful.
Benefits Offered by Cloud-Based CRM Software
Cost Efficient: Because there is no heavy investment needed in hardware or other IT infrastructure, there are savings from the maintenance and support end.
Scalability: Such systems can scale up at the same pace as the companies do, automatically increasing data storage or end-user capacity along with business growth.
Enhanced Collaboration: There would be a real-time view of customer data so that team members across locations could work on a task together.
Data Security: Top cloud CRM vendors provide tight security protocols like encryption and multi-factor authentication.
Improved Customer Satisfaction: It is always a case of personalized interactions and timely communication leading to better customer relationships.
Employees Working on CRMS from the Cloud
Salesforce: Because of all its great features, scalability, and customizations, it is known as best for giants in the industry.
HubSpot CRM: This is the simplest free CRM for small and medium companies.
Zoho CRM: Very nicy pricing plans and powerful automation integrated with strong AI capabilities.
Pipedrive: Great for a sales team's intuitive management of pipelines.
Freshsales from Freshworks: A blend of CRM features with AI-powered insights and automations.
How to Choose the Best Cloud CRM Software
You need to discuss the following factors when looking for a CRM solution:
Business Size and Requirements: Choose CRM based on the size of your company and the goals that you want to achieve with it.
Integration Support: Have it well connected to your already existing tools.
User Experience: Go for an easy to navigate interface that provides your people with fairly easy acclimatization.
Customizable Options: Go for a platform that allows the flow of work to be modified according to your business.
Security and Compliance: Check that the CRM is compliant to the requirements for data protection.
Conclusion
Cloud Based CRM Software investment is no longer optional; it is compulsory for most businesses seeking better relations with their customers and eventually ordering their operations. These will ensure that companies work more efficiently, increase their sales volumes, and deliver customer experiences that will convert. Critically analyze your business needs before deciding on the best CRM platform for growth and success optimization.
0 notes
Text
ATM Security Market Overview: Trends and Growth Drivers
Introduction
The global ATM security market has experienced significant growth in recent years, driven by the increasing deployment of automated teller machines (ATMs) worldwide. As financial institutions and businesses rely more on ATMs to provide convenient banking services, the need for robust security measures has become paramount. Rising incidences of cyber threats, fraud, and physical attacks on ATMs have fueled the demand for advanced security solutions. This article explores the key trends and growth drivers shaping the ATM security market.

Market Overview
The ATM security market encompasses a wide range of solutions designed to protect ATMs from fraud, cyberattacks, and physical threats. These solutions include hardware-based security such as surveillance cameras, alarm systems, biometric authentication, and anti-skimming devices, as well as software-based security solutions like encryption, firewall protection, and AI-powered threat detection.
Key Trends in ATM Security
1. Rising Cyber Threats and Fraud Prevention
One of the most significant trends in the ATM security market is the growing threat of cyberattacks. Cybercriminals are using sophisticated methods such as malware attacks, jackpotting, and phishing to compromise ATMs and steal sensitive financial information. Financial institutions are increasingly investing in advanced security software, including AI-driven fraud detection and real-time monitoring systems, to combat these threats.
2. Adoption of Biometric Authentication
Biometric authentication, including fingerprint recognition, facial recognition, and iris scanning, is gaining traction in the ATM security space. This technology enhances security by ensuring that only authorized users can access ATM services. Biometric-enabled ATMs help prevent card skimming and unauthorized transactions, offering a higher level of security compared to traditional PIN-based authentication.
3. Integration of AI and Machine Learning
Artificial intelligence (AI) and machine learning are playing a crucial role in enhancing ATM security. These technologies enable predictive analytics, allowing financial institutions to detect suspicious activities and potential fraud attempts in real time. AI-powered solutions can analyze transaction patterns and flag anomalies, helping banks mitigate risks proactively.
4. Enhanced Physical Security Measures
Physical security measures remain a crucial aspect of ATM security. Solutions such as reinforced enclosures, anti-skimming devices, and intelligent surveillance systems are being widely adopted. Smart ATMs are now equipped with self-defense mechanisms, including ink-staining technology to mark stolen cash and GPS tracking systems to locate stolen ATMs.
5. Shift Towards Cloud-Based Security Solutions
The shift towards cloud-based security solutions is another notable trend in the ATM security market. Cloud-based security platforms provide centralized monitoring, enabling financial institutions to manage security across multiple ATM locations efficiently. These solutions offer real-time threat detection, automatic software updates, and improved scalability.
6. Regulatory Compliance and Standards
Governments and regulatory bodies worldwide are implementing stringent security regulations for ATMs to protect consumer data and financial transactions. Compliance with standards such as PCI DSS (Payment Card Industry Data Security Standard) and EMV (Europay, Mastercard, and Visa) requirements has become mandatory for ATM operators, driving the adoption of advanced security solutions.
Growth Drivers of the ATM Security Market
1. Increasing ATM Deployment Worldwide
Despite the rise of digital banking, ATMs continue to be a vital part of the financial ecosystem. The increasing number of ATMs in developing regions, particularly in Asia-Pacific and Africa, is driving the demand for security solutions. As banks expand their ATM networks, they are also investing in enhanced security to protect against evolving threats.
2. Rising Incidences of ATM Fraud
The surge in ATM-related fraud incidents, including skimming, card cloning, and cyberattacks, has prompted financial institutions to invest heavily in security measures. The growing awareness among consumers and businesses about fraud risks is further propelling the demand for secure ATM solutions.
3. Technological Advancements
The continuous evolution of security technologies, including AI, blockchain, and IoT-enabled security solutions, is accelerating the growth of the ATM security market. Innovations such as real-time transaction monitoring, end-to-end encryption, and biometric authentication are becoming industry standards.
4. Growing Adoption of Contactless and Cardless Transactions
The rise of contactless and cardless ATM transactions is reducing the risk of card skimming and fraud. Banks are integrating QR code scanning, mobile-based authentication, and NFC (Near Field Communication) technology to enhance ATM security while offering a seamless customer experience.
5. Investment in Smart ATMs
Banks and financial institutions are investing in next-generation smart ATMs that offer advanced security features. Smart ATMs are equipped with AI-driven security, biometric authentication, and enhanced encryption, making them less vulnerable to cyber and physical attacks.

Challenges in the ATM Security Market
While the ATM security market is witnessing robust growth, there are challenges that need to be addressed:
High Implementation Costs: Advanced security solutions require significant investment, which can be a barrier for smaller financial institutions.
Evolving Cyber Threats: Cybercriminals are constantly developing new tactics to bypass security measures, requiring continuous updates and upgrades.
Consumer Resistance to Biometric Authentication: Some users may be hesitant to adopt biometric authentication due to privacy concerns and lack of awareness.
Conclusion
The ATM security market is evolving rapidly, driven by increasing cyber threats, regulatory compliance, and technological advancements. Financial institutions are prioritizing security investments to safeguard ATMs against fraud and attacks. The adoption of biometric authentication, AI-driven fraud detection, and cloud-based security solutions is shaping the future of ATM security. As the global financial landscape continues to evolve, ensuring robust security for ATMs will remain a top priority for banks and financial service providers.
The ongoing innovations and regulatory measures will further drive the demand for comprehensive ATM security solutions, making the market a key focus area for security providers and financial institutions alike.
0 notes
Text
Global Network Encryption Market Report (2025–2033): Industry Trends, Growth, Share, Size, and Forecast
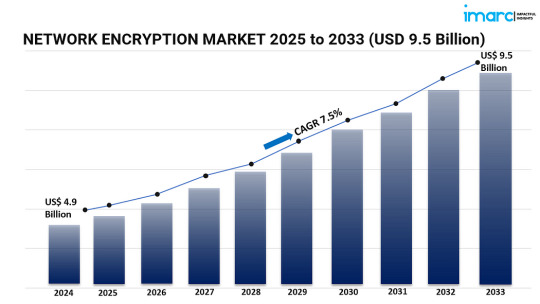
Market Overview:
The global network encryption market reached a valuation of USD 4.9 billion in 2024. Projections indicate that it will grow to USD 9.5 billion by 2033, reflecting a compound annual growth rate (CAGR) of 7.5% from 2025 to 2033. This growth is driven by the escalating demand for 5G networks, the imperative for digitalization, and the increasing prevalence of cybersecurity threats. These factors collectively underscore the critical need for robust network encryption solutions to safeguard sensitive data across various sectors.
Study Assumption Years:
Base Year: 2024
Historical Years: 2019–2024
Forecast Years: 2025–2033
Network Encryption Market Key Takeaways:
Market Size and Growth: The network encryption market was valued at USD 4.9 billion in 2024 and is projected to reach USD 9.5 billion by 2033, exhibiting a CAGR of 7.5% during the forecast period.
Regional Dominance: North America leads the market, attributed to the rapid expansion of startups and SMEs, coupled with robust technological advancements.
Component Segmentation: The market is segmented into hardware, solutions, and services, each catering to specific security needs across industries.
Deployment Modes: Organizations are adopting both cloud-based and on-premises deployment modes to enhance data security.
Organizational Adoption: Both small and medium-sized enterprises (SMEs) and large enterprises are increasingly implementing network encryption to protect sensitive information.
End-Use Industries: Key sectors such as telecom and IT, BFSI, government, and media and entertainment are major adopters of network encryption solutions.
Request for a sample copy of this report: https://www.imarcgroup.com/network-encryption-market/requestsample
Market Growth Factors:
Growing Cybersecurity Threats: The rising level of cyber threats and data breaches has created a vital need for network encryption solutions. Organizations are more concerned about protecting sensitive data in transit to avert unauthorized access and possible financial losses. This increased emphasis on cybersecurity is a major force driving the deployment of advanced encryption technologies.
The Expansion of 5G Networks: The global deployment of 5G networks is inducing tremendous changes in speed and connectivity of data transfer. But with this advancement comes more security challenges that are necessitating good considerations of encryption methods to protect the way data will flow. Network encryption solutions are thus needed in the 5G environment to help in maintaining data integrity and privacy.
Regulatory Compliance and Digitalization: With an ongoing digital transformation, upholding stricter regulatory standards for data protection is paramount. Compliance with regulations such as GDPR and HIPAA demands organizations to implement strong encryption solutions to protect data confidentiality and avoid legal ramifications. This regulatory environment, hence, forms a key part of the network encryption market growth process.
Market Segmentation:
Breakup by Component:
Hardware: Physical devices designed to encrypt data at various network layers, ensuring secure transmission.
Solutions: Software-based applications providing encryption protocols and management tools to protect data across networks.
Services: Professional and managed services offering implementation, maintenance, and support for encryption systems.
Breakup by Deployment Mode:
Cloud-based: Encryption solutions hosted on cloud platforms, offering scalability and remote accessibility.
On-premises: Encryption systems installed within an organization’s infrastructure, providing direct control over security measures.
Breakup by Organization Size:
Small and Medium-sized Enterprises: SMEs adopting encryption to protect sensitive data and comply with industry regulations.
Large Enterprises: Organizations with extensive networks implementing advanced encryption to safeguard vast amounts of data.
Breakup by End Use Industry:
Telecom and IT: Securing communication networks and data centers against cyber threats.
BFSI: Protecting financial transactions and customer information from unauthorized access.
Government: Ensuring the confidentiality of sensitive governmental data and communications.
Media and Entertainment: Safeguarding digital content and intellectual property rights.
Others: Industries such as healthcare and retail implementing encryption to protect sensitive data.
Breakup by Region:
North America (United States, Canada)
Asia Pacific (China, Japan, India, South Korea, Australia, Indonesia, Others)
Europe (Germany, France, United Kingdom, Italy, Spain, Russia, Others)
Latin America (Brazil, Mexico, Others)
Middle East and Africa
Regional Insights:
North America dominates the network encryption market, driven by the rapid expansion of startups and SMEs, increasing investment in cybersecurity, and the early adoption of advanced encryption technologies. The United States leads the market due to stringent data protection regulations and a high concentration of IT and telecom companies. The region’s emphasis on securing sensitive government and financial data further fuels market growth.
Recent Developments & News:
The network encryption market has witnessed significant technological advancements, including the integration of AI-driven security solutions and quantum encryption. Recent developments focus on enhancing encryption algorithms to counter evolving cyber threats. Additionally, several cybersecurity firms are investing in research and development to strengthen data protection. The growing adoption of zero-trust security frameworks and cloud-based encryption solutions is shaping the industry’s future. The emergence of post-quantum cryptography further highlights the market’s shift toward next-generation security protocols.
Key Players:
Atos SE
Ciena Corporation
Cisco Systems Inc.
Colt Technology Services Group Limited
F5 Networks Inc.
International Business Machines Corporation (IBM)
Juniper Networks Inc.
Nokia Corporation
PacketLight Networks Ltd.
Raytheon Technologies Corporation
Rohde & Schwarz GmbH & Co KG
Securosys SA
Senetas Corporation Limited
Thales Group
Viasat Inc.
If you require any specific information that is not covered currently within the scope of the report, we will provide the same as a part of the customization.
Ask Analyst for Customization: https://www.imarcgroup.com/request?type=report&id=4969&flag=C
About Us:
IMARC Group is a global management consulting firm that helps the world’s most ambitious changemakers to create a lasting impact. The company provide a comprehensive suite of market entry and expansion services. IMARC offerings include thorough market assessment, feasibility studies, company incorporation assistance, factory setup support, regulatory approvals and licensing navigation, branding, marketing and sales strategies, competitive landscape and benchmarking analyses, pricing and cost research, and procurement research.
0 notes
Text
Data Diode Market Expansion: $4.1B to $10.5B by 2034 🔐
Data Diode Market is set for exponential growth, expanding from $4.1 billion in 2024 to $10.5 billion by 2034, at a CAGR of 9.9%. With the surge in cybersecurity threats, data diodes have become essential for secure, one-way data transmission, safeguarding critical infrastructure, defense systems, and financial institutions.
To Request Sample Report: https://www.globalinsightservices.com/request-sample/?id=GIS10572 &utm_source=SnehaPatil&utm_medium=Article
Key Market Drivers & Trends
🔹 Industrial control systems & government networks lead market adoption, ensuring secure communication & compliance. 🔹 Military & defense applications rank second, reflecting heightened national security priorities. 🔹 Financial services & energy sectors are rapidly adopting data diodes to prevent cyber attacks & ensure data integrity. 🔹 North America dominates, driven by robust cybersecurity policies & advanced infrastructure. 🔹 Europe follows closely, with stringent data protection regulations & increasing security investments. 🔹 Asia-Pacific is a high-growth region, fueled by rapid digital transformation & rising cyber threats.
Market Segmentation Overview
🛡 Types: Unidirectional, Bidirectional 💻 Products: Hardware Data Diodes, Software Data Diodes 🛠 Services: Installation, Maintenance, Consulting 📡 Applications: Industrial Control, Government, Military, Telecommunications, Healthcare 🏢 End Users: BFSI, Defense, Aerospace, Oil & Gas, Healthcare 🌐 Deployment: On-Premise, Cloud-Based, Hybrid
In 2024, the market witnessed 1.2 million units, projected to reach 2.5 million by 2028. The industrial sector leads with a 45% share, followed by government (30%) and defense (25%). Owl Cyber Defense, BAE Systems, and Advenica dominate with cutting-edge innovations in cross-domain security solutions.
With the rising cyber threat landscape, stringent regulations, and expanding digital infrastructures, the Data Diode Market is set to redefine network security for the future. 🔐💡
#DataDiode #CyberSecurity #DataProtection #CriticalInfrastructure #IndustrialSecurity #NetworkSecurity #SecureDataTransfer #CyberDefense #MilitaryTech #ITSecurity #FinancialCyberSecurity #IoTSecurity #GovernmentCyberSecurity #CloudSecurity #ThreatDetection #Encryption #DigitalTransformation #SecureNetworks #CyberResilience #SmartDefense #TechnologyTrends #InformationSecurity #AIinCyberSecurity #SecuritySolutions #ZeroTrust #NextGenSecurity
0 notes
Text
Payment Processing Solutions Market Business Overview and Planning 2025-2032

Payment processing solutions are technologies that enable merchants to accept payments for goods and services. They include software, hardware, and services that handle the entire process of receiving and managing electronic payments, from initiation to settlement. These solutions typically include point-of-sale (POS) terminals, online payment gateways, mobile payment systems, and various fraud protection and security services.
The payment processing industry has witnessed significant developments with the rise of digitalization, leading to more efficient, secure, and user-friendly systems. Payment processors work in coordination with banks, financial institutions, and other service providers to enable smooth transactions across multiple platforms, including mobile apps, websites, and physical stores.
Market Size and Growth Outlook (2025-2032)
Payment processing market size in 2024 was valued at USD 111.6 Billion in 2024. It is projected to grow at a robust CAGR of 9.2% from 2025 to 2032, reaching USD 225.61 Billion by 2032.
Several factors are driving this growth:
Digital Transformation: As businesses increasingly adopt e-commerce and digital payment systems, the demand for efficient, scalable, and secure payment processing solutions has surged.
Mobile Payment Trends: With the widespread use of smartphones, mobile payment solutions like Apple Pay, Google Pay, and Samsung Pay are gaining traction. These mobile-first solutions are projected to become the primary form of payment in many regions.
Shift to Cashless Societies: Governments, especially in developed economies, are pushing for a cashless society, which accelerates the adoption of digital payment methods.
Cross-border E-commerce: As online shopping grows globally; payment processors must adapt to handle multi-currency transactions and offer international payment solutions.
Blockchain and Cryptocurrency Integration: The integration of blockchain technology and cryptocurrencies like Bitcoin is expected to become a significant trend in the payment processing industry. These technologies are expected to lower transaction costs, increase speed, and improve security.
Request Sample of the Report - https://www.skyquestt.com/sample-request/payment-processing-solutions-market
Key Market Segments
The payment processing solutions market can be segmented by solution type, deployment mode, end-users, and geography.
By Solution Type
Point-of-Sale (POS) Solutions: POS systems remain one of the most significant components of the payment processing market. Innovations in contactless payment solutions have also enhanced POS technology, driving increased adoption among merchants.
Payment Gateways: Payment gateways are expected to grow rapidly with the rise of e-commerce and mobile transactions. These systems allow customers to make secure payments on websites and mobile apps.
Mobile Payment Solutions: Mobile wallets and apps continue to lead the growth in digital payment methods. Mobile payment processing enables customers to make purchases on-the-go, adding convenience and speed to transactions.
Fraud Prevention and Security Solutions: As cyber threats increase, security is a major concern for payment processing providers. Companies are investing heavily in anti-fraud measures, encryption technologies, and multi-factor authentication systems.
By Deployment Mode
On-premises Solutions: These are traditional systems where merchants deploy payment processing hardware and software within their premises.
Cloud-based Solutions: Cloud-based payment processing solutions are gaining popularity due to their scalability, flexibility, and ease of integration with other digital tools. These solutions reduce upfront infrastructure costs and provide access to real-time data analytics.
By End-User
Retail: Retailers, both large and small, are major consumers of payment processing systems. The demand for quick and secure transactions continues to rise in physical and online stores.
E-commerce: With the rapid growth of online shopping, e-commerce businesses are at the forefront of adopting payment processing technologies to offer smooth checkout experiences.
Banking and Financial Institutions: Financial services providers and banks integrate payment processing solutions into their operations to facilitate fund transfers, bill payments, and other customer transactions.
Healthcare and Others: Sectors like healthcare, education, travel, and hospitality are also increasingly adopting payment processing solutions to meet customer demands for frictionless payments.
Want to customize this report? - https://www.skyquestt.com/speak-with-analyst/payment-processing-solutions-market
Regional Analysis
North America: North America holds the largest share of the payment processing market, driven by high adoption rates of digital payments, advancements in mobile payment technology, and a growing e-commerce sector. The United States is a leader in the implementation of digital payment systems, with several fintech companies dominating the market.
Europe: Europe is expected to witness significant growth in the payment processing sector, especially due to the European Union’s initiatives toward digital financial systems and cashless payments. The UK, Germany, and France are expected to be key contributors to the region's growth.
Asia Pacific: Asia Pacific is projected to experience the fastest growth in the payment processing solutions market. Countries like China, India, and Japan are at the forefront of mobile payment adoption, driving a large portion of regional market expansion.
Latin America and Middle East & Africa: Latin America and the Middle East are experiencing increased mobile payment adoption and rising digital payment penetration, making them emerging markets for payment processing solutions.
Key Trends and Drivers
Artificial Intelligence and Machine Learning: Payment processors are integrating AI and ML to offer enhanced fraud detection, personalized customer experiences, and efficient payment routing.
Biometric Authentication: As security concerns grow, biometric technologies like facial recognition and fingerprint scanning are being used to authorize transactions, enhancing safety and convenience.
Contactless Payments: The demand for contactless payments is growing, especially post-pandemic, as consumers prefer touch-free transactions for safety and convenience.
Regulatory Changes: The introduction of regulations like PSD2 in Europe and various other national regulations around digital payments is expected to shape the payment processing market, with an increased focus on security and transparency.
Get insights into Trends, Challenges and Companies @ https://www.skyquestt.com/report/payment-processing-solutions-market
Competitive Landscape
The payment processing market is highly competitive, with both established players and emerging fintech companies playing a significant role. Key players include:
PayPal
Fiserv
FIS
ACI Worldwide
Square (Block)
Mastercard
Visa
Stripe
PhonePe
Razorpay
These companies are continuously innovating and expanding their offerings through acquisitions, partnerships, and the development of new technologies to maintain a competitive edge in the market.
Future Outlook
The payment processing solutions market is on a path of rapid growth, driven by the global shift toward digital and mobile payments. With technological advancements, regulatory changes, and a growing preference for cashless transactions, the market is poised to expand significantly over the next decade. Businesses across industries must stay ahead of these trends to ensure seamless, secure, and efficient payment processing solutions for their customers.By 2032, the payment processing market is expected to become a central pillar of global financial ecosystems, with innovations continuing to shape the landscape of transactions worldwide.
#Asia Payment Processing Solutions Market#Europe Payment Processing Solutions Market#Middle East Payment Processing Solutions Market Size#North America Payment Processing Solutions Market
0 notes
Text
Crucial MX500 1TB 3D NAND SATA SSD 2.5" Internal Drive
Crucial MX500 1TB 3D NAND SATA SSD 2.5" Internal Drive Review: The Perfect Balance of Performance and Value
When it comes to upgrading your PC or laptop, one of the best investments you can make is swapping out an old hard drive for a solid-state drive (SSD). SSDs offer faster boot times, improved data transfer rates, and a more responsive overall system. Among the many SSD options available, the Crucial MX500 1TB 3D NAND SATA SSD stands out as a top choice for those looking for a solid, reliable, and budget-friendly upgrade. In this article, we’ll take a closer look at the Crucial MX500 and explore its features, performance, and value proposition.

Overview: A Powerhouse at a Reasonable Price The Crucial MX500 1TB 3D NAND SATA SSD is part of Crucial's widely respected MX500 series. This drive offers a perfect blend of speed, durability, and affordability, making it a go-to solution for anyone seeking to improve their system’s performance. It’s built with 3D NAND technology, which allows for more data storage in less space, leading to improved reliability and efficiency.
Key Features 1TB Storage Capacity: With 1TB of storage, this SSD offers ample space for a range of applications, games, and data. Whether you're a casual user or a gamer with large libraries, the Crucial MX500 has more than enough room for your needs. It strikes a balance between storage space and performance, making it suitable for everything from daily computing to heavy-duty tasks.
3D NAND Flash Technology: The use of 3D NAND technology enhances the overall performance and reliability of the drive. 3D NAND allows for a higher density of cells, meaning you get more storage in a smaller space. It also helps improve endurance and maintain consistent performance over time, reducing the risk of wear and tear on the SSD.
SATA III Interface: The Crucial MX500 connects via a SATA III interface (6Gb/s), which ensures compatibility with most modern desktops and laptops. While SATA III is not as fast as NVMe (which uses PCIe), it still offers impressive speeds that will significantly improve the overall performance compared to traditional HDDs.
Sequential Read/Write Speeds: One of the standout features of the MX500 is its speed. The drive offers sequential read speeds of up to 560MB/s and sequential write speeds of up to 510MB/s. These speeds are ideal for speeding up boot times, launching programs, and transferring files. While not the absolute fastest on the market, the MX500's speeds are more than sufficient for most users and provide a noticeable performance boost over older hard drives.
Integrated Power Loss Immunity: A unique feature of the MX500 is its power loss immunity. This technology ensures that if the power goes out unexpectedly, the drive will protect your data. It uses a capacitor to provide enough power to the SSD to safely save data, reducing the likelihood of corruption in the event of a sudden shutdown.
Hardware Encryption Support: The MX500 includes AES 256-bit hardware encryption to safeguard your sensitive data. This encryption ensures that your files are kept secure, especially in business environments or when handling personal information. It operates seamlessly without any impact on performance, adding a layer of protection without slowing you down.
Low Power Consumption: The Crucial MX500 is designed to be energy efficient. This helps to extend the battery life of laptops and reduce the overall power consumption of your desktop system.
Performance When compared to traditional hard drives (HDDs), the Crucial MX500 1TB SSD offers a massive improvement in speed and performance. Boot times are faster, and the drive dramatically shortens load times for games, apps, and data transfers. The 560MB/s read speed and 510MB/s write speed are excellent benchmarks for a SATA-based SSD. While NVMe SSDs may offer faster speeds, the difference is often negligible for everyday tasks. In practical use, users will find that the MX500 delivers an excellent balance of speed and efficiency for both personal and professional applications.
Endurance and Reliability The Crucial MX500 is built to last. Thanks to its 3D NAND technology, it boasts impressive endurance, with up to 360 TBW (terabytes written). This means you can write up to 360 terabytes of data to the drive over its lifetime before you might see a noticeable degradation in performance. For typical users, this will translate into many years of reliable service. Additionally, the drive includes integrated S.M.A.R.T. monitoring and thermal throttling features to protect against overheating, ensuring the drive operates within safe temperature ranges.
Easy Installation Installing the Crucial MX500 is straightforward, and the drive comes with software tools to assist with the setup. Crucial Storage Executive is a free tool that allows you to manage your drive, perform firmware updates, and monitor the health and performance of your SSD. Additionally, Acronis True Image software is included for easy migration of your operating system and files from your old hard drive to the new SSD.
Pricing and Value One of the biggest draws of the Crucial MX500 1TB SSD is its price. It provides high-end features at a price that’s affordable for the average consumer. At the time of writing, the 1TB version is priced competitively, making it an excellent value for anyone looking to upgrade their storage without breaking the bank. It offers much of the performance and reliability of more expensive SSDs but at a more budget-conscious price point.
Final Thoughts The Crucial MX500 1TB 3D NAND SATA SSD is an excellent choice for anyone looking to improve the performance of their computer without spending a fortune. With fast speeds, 3D NAND technology, robust endurance, and enhanced data protection features, this drive delivers the best of both worlds: performance and value. Whether you're upgrading an old laptop or boosting the storage of a desktop, the MX500 is sure to provide a noticeable improvement in speed and overall user experience. For those looking for a reliable and budget-friendly upgrade, the Crucial MX500 is hard to beat.
#CrucialMX500#1TBSSD#3DNANDtechnology#SATA3SSD#InternalSSD#PCupgrade#SSDreview#SolidStateDrive#CrucialSSD#SSDperformance#Fastboottimes#SATAIII#Datasecurity#Powerlossimmunity#Encryption#AcronisTrueImage#Thermalthrottling#Lowpowerconsumption
0 notes
Text
The Quantum Computing Market is projected to grow from USD 1305 million in 2024 to an estimated USD 12472.6 million by 2032, with a compound annual growth rate (CAGR) of 32.6% from 2024 to 2032. Quantum computing, a technological frontier once confined to the realms of theoretical physics and research laboratories, is now at the cusp of transforming industries worldwide. With its unparalleled ability to process massive amounts of data at unimaginable speeds, the quantum computing market is poised to redefine how businesses solve complex problems, optimize operations, and innovate.
Browse the full report at https://www.credenceresearch.com/report/quantum-computing-market
Market Overview
The global quantum computing market has been growing rapidly, with analysts projecting a compound annual growth rate (CAGR) of over 30% from 2023 to 2030. Valued at approximately $1.5 billion in 2022, the market is expected to exceed $10 billion by the end of this decade. Factors driving this growth include increasing government investments, rising demand for advanced computing solutions, and the growing need for high-performance computing in sectors such as healthcare, finance, and defense.
Key Drivers of Market Growth
Advancements in Hardware Quantum computers rely on qubits, which leverage quantum mechanical principles such as superposition and entanglement. Hardware innovations from companies like IBM, Google, and Rigetti Computing are making quantum systems more stable and scalable, a critical factor for their commercialization.
Government and Private Investments Governments worldwide are pouring billions into quantum research. The U.S., China, and the European Union lead the race, with programs such as the National Quantum Initiative Act and China’s Quantum Science Satellite Project. Meanwhile, tech giants like Microsoft and Amazon, alongside startups, are also investing heavily in quantum technologies.
Expanding Applications Quantum computing is not just about faster calculations; its applications span various industries:
Healthcare: Revolutionizing drug discovery by simulating molecular interactions at quantum levels.
Finance: Enhancing risk analysis, fraud detection, and portfolio optimization.
Defense: Developing cryptographic systems that are resistant to hacking.
Energy: Optimizing power grids and advancing battery technology.
Challenges and Roadblocks
Despite its promise, quantum computing faces several hurdles:
Technological Limitations: Maintaining qubit stability (coherence) remains a significant challenge.
High Costs: Quantum systems are expensive to develop, maintain, and operate.
Lack of Skilled Workforce: The market suffers from a shortage of professionals with expertise in quantum mechanics and computer science.
Security Concerns: The advent of quantum computers poses a threat to current encryption methods, necessitating a transition to quantum-safe cryptography.
Future Outlook
The quantum computing market is set to experience exponential growth as researchers overcome existing challenges and commercial adoption increases. Hybrid models, integrating classical and quantum computing, are expected to emerge as a practical solution for near-term applications.
Furthermore, the rise of quantum-as-a-service (QaaS) platforms will democratize access to quantum technology, allowing businesses of all sizes to explore its potential. The healthcare and finance sectors are likely to witness the most significant transformations, with breakthroughs in drug discovery and financial modeling leading the charge.
Key Player Analysis:
Accenture Plc.
D-WaveSystem Inc.
Google LLC
IBM Corporation
Intel Corporation
Microsoft Corporation
Quantinuum Ltd.
Rigetti & Co, Inc.
Riverlane
Zapata Computing
Segmentation:
By Component
Hardware
Software
By Deployment
On-premise
Cloud
By Application
Machine Learning
Optimization
Biomedical Simulations
Financial Services
Electronic Material Discovery
Traffic Optimization
Weather Forecasting
Others
By End-user
Healthcare
Banking, Financial Services and Insurance (BFSI)
Automotive
Energy and Utilities
Chemical
Manufacturing
Others
By Region
North America
U.S.
Canada
Mexico
Europe
Germany
France
U.K.
Italy
Spain
Rest of Europe
Asia Pacific
China
Japan
India
South Korea
South-east Asia
Rest of Asia Pacific
Latin America
Brazil
Argentina
Rest of Latin America
Middle East & Africa
GCC Countries
South Africa
Rest of the Middle East and Africa
Browse the full report at https://www.credenceresearch.com/report/quantum-computing-market
About Us:
Credence Research is committed to employee well-being and productivity. Following the COVID-19 pandemic, we have implemented a permanent work-from-home policy for all employees.
Contact:
Credence Research
Please contact us at +91 6232 49 3207
Email: [email protected]
0 notes
Text
Cyber Security Market - Forecast(2024 - 2030)
Cyber Security Market Overview

Request Sample Report :
The telecom organizations are adopting advanced cyber security solutions such as real-time security monitoring, instant cyber posture visibility, and rapid threat resolution to prevent the cyber-attack on telecom networks. Along with the telecom sector, the aerospace industry is considered to be another key end-users to cyber security market. The aerospace and defense industry are prone to cyber-attack due to its continuous exposure to non-A&D, OT-based technologies.
Thus, this industry is adopting advanced cybersecurity solution to enhance protection against cybercrime. The rising need for solutions ranging from antivirus software, unified threat management system, next-generation firewalls, DNS filtering, malware protection and threat intelligence will drive the demand for cyber security. One prominent trend in the cyber security market is the increasing adoption of Zero Trust Architecture (ZTA). This approach challenges the traditional perimeter-based security model by assuming that threats can originate from both inside and outside the network. ZTA emphasizes strict identity verification and access controls, requiring continuous authentication and authorization for every user and device attempting to access resources. With the proliferation of cloud services, remote work, and mobile devices, organizations are realizing the limitations of perimeter defenses alone. As a result, they are turning to ZTA to bolster their defenses and mitigate the risks associated with insider threats, unauthorized access, and advanced persistent threats.
Inquiry Before Buying :
The growing recognition of ZTA’s effectiveness in enhancing security posture is driving significant investment in Zero Trust solutions across various industries. Another key trend shaping the cyber security market is the increasing integration of artificial intelligence (AI) and machine learning (ML) technologies for threat detection and response. As cyber threats become more sophisticated and prevalent, organizations are turning to AI-driven solutions to augment their security operations. AI and ML algorithms can analyze vast amounts of data in real-time, enabling early detection of anomalies, unusual patterns, and potential security breaches. These technologies empower security teams to identify and respond to threats more efficiently, reducing detection and response times. Moreover, AI-driven security solutions can automate repetitive tasks, freeing up security personnel to focus on more strategic initiatives. With the continuous evolution of cyber threats, the demand for AI-powered security tools and platforms is expected to grow, driving innovation and investment in the development of advanced threat detection and response capabilities.
Market Snapchat
Cyber Security Market Report Coverage
The report: “Cyber Security Market Forecast (2024–2030)”, by IndustryARC, covers an in-depth analysis of the following segments of the Cyber Security System Market.
By Component: Cyber Security Software, Cyber Security Hardware, Cyber Security Services.
By Deployment: On-Premise and Cloud.
By Security Type: Network & Endpoint Security, Internet of Things/Industrial Internet of Things Security, Threat Intelligence, Mobile Security, Behavioral Detection, Cloud Security, Deception Security and Others.
By Organization Size: SME, Large Enterprise.
By Solution: Antivirus, UTM, SIEM, DDOS Mitigation, Disaster Recovery, Firewall, DLP, Web Filtering, Threat Intelligence, IAM, Risk and Compliance Management, IDS, Encryption and Others.
By Industry Vertical: Aerospace, Government, Financial Services, Healthcare, Telecommunications, Automobile, Information Technology sector and others
Schedule A Call :
By Geography: North America (U.S, Canada, Mexico), Europe(Germany, UK, France, Italy, Spain, Russia, Netherlands, Denmark and Others), APAC(China, Japan India, South Korea, Australia, Taiwan, Malaysia and Others), South America(Brazil, Argentina, Ecuador, Peru, Colombia, Costa Rica and others), and RoW (Middle east and Africa)
Key Takeaways
• In 2023, the Cyber Security market was dominated by North America owing to the increasing use of prevalent technology which has raised the risk of cyber threat leading to the need for cybersecurity solutions.
• The rising demand for cloud-based cybersecurity solutions in order to store and secure data during data loss or data breaches has driven the growth of the market
• The rapid advancement of artificial intelligence leading to the introduction of technologies such as machine learning and deep learning which will enhance the growth of the market.

For More Details on This Report — Request for Sample
Cyber Security Market Segment Analysis — By Deployment
Cloud segment held the largest market share of 53.1% in the Cybersecurity market in 2023. The growing of massive store applications in order to store and secure data with advanced security methods are driving the need for cloud-based security solutions. As cloud-based cybersecurity solutions offers social networking privacy, online storage, system optimization and so on. Furthermore, the rising demand for online cloud storage leads to provide backup and restorations of data caused due to data breaches or data loss. These significant advantages of cloud technology will lead to surge the growth of the market.
Cyber Security Market Segment Analysis — By Industry Vertical
The telecom sector is estimated to grow at a CAGR of 10.2% during the forecast period 2023–2030. The GSM Association (GSMA) predicted that quantum computing will be a destabilizer for the telecom sector, making Public Key Infrastructure (PKI) obsolete in the near future. Telecommunication companies are in plans of implementing quantum-safe cryptography algorithms to mitigate cyber-attacks. In order to control cyber-attacks, the European Union (EU) has introduced many regulations such as the Network and Information Security Directive (NISD) and the General Data Protection Regulations (GDPR). NISD is yet to be implemented which requires core digital infrastructure operators and certain digital service providers to ensure that their network and information systems meet minimum standards of cybersecurity. These regulations are implemented to achieve and maintain high network security, and ensure obligatory reporting during any incidents.
Cyber Security Market Segment Analysis — By Geography
In 2023, North America dominated the Cyber Security market with a share of more than 40.2%, followed by Europe and APAC. The growing use of technology and data has led to the rise of most vulnerable cyber threats and crimes which is leading to the growth of this market in this region. Also, the financial stability in this region has allowed organization to invest in cybersecurity for providing security of data and software. These developments are propelling the growth of cybersecurity market in North America.
Cyber Security Market Drivers
Rising importance Artificial Intelligence (AI)
The rising advancement in artificial intelligence is leading to the introduction of machine learning technologies into products which includes cybersecurity. Moreover, technologies such as deep learning are being used for face detection, natural language processing, threat detection, and others concepts. Also, the acceleration of artificial intelligence (AI) has led to the identification of new threats and helps in responding and block cyber-attacks in an organization. Hence, the deployment of artificial intelligence technologies will further drive the growth of the cybersecurity market.
Increasing need for Cybersecurity in Aerospace
Aerospace industry is widely developing with the integration of new technology such as advanced navigation and guidance systems. This system are used in airplanes which are highly vulnerable to cyber-attacks, which have irrevocable repercussions. So, the rising risk of cyber-attacks and the increasing need to protect the computer networks in the air are leading to the rise of investment in the security infrastructure. Thus, the rising investment by aerospace industry in the security infrastructure has led to the requirement of cybersecurity further boosting the growth of the market.
Cyber Security Market Challenges
Revolution of Blockchain and IoT Threats
The rising demand for Blockchain systems has made it difficult to predict the rising cyber threats which is hindering the cybersecurity market. Furthermore, the increasing usage of IoT has led to the growing number of IoT threats, as IoT includes the connection of physical devices which have a unique identifier (UID). These devices has the ability to transfer data over a network without any human interference and human to computer interaction. Thus, the software and firmware which are required to run these IoT devices make the user more susceptible to cyber-attacks further hindering the growth of the market.
Buy Now :
Cyber Security Market Landscape
Technology launches, acquisitions and R&D activities are key strategies adopted by players in the Cyber Security market. In 2023, the market of Cyber Security has been consolidated by the major players — AWS, Check Point Software Technologies, NTT Security, Cisco Systems, CyberArk, FireEye, IBM Corporation, Oracle, Microsoft and Juniper Networks.
Acquisitions/Technology Launches
In December 2023, Multinational conglomerate Honeywell has agreed to buy Carrier’s Global Access Solutions business for $4.95 billion in cash. The acquisition will strengthen Honeywell’s core security offerings with the addition of hardware and software properties
In Nov 2023, US-based data security company Rubrik has launched Ruby, its generative AI extension for Rubrik Security Cloud, which will speed up cyber threat detection, recovery and resilience. In response to data risk alerts generated in Rubrik Security Cloud, users can interact with Ruby, the company’s AI assistant, ask follow-up questions including whether any sensitive data was impacted, or what needs to be done to restore the environment.
For more Information and Communications Technology Market reports, please click here
#CyberSecurity#InfoSec (Information Security)#DataProtection#CyberThreats#DigitalSecurity#CyberAwareness#TechSecurity
0 notes
Text
Medical Alert Systems Market Market Outlook 2025: Trends, Opportunities, and Forecasts
In an increasingly aging global population, health and safety are paramount concerns for both individuals and caregivers. The Medical Alert Systems Market has emerged as an essential part of modern healthcare technology, providing peace of mind and real-time emergency assistance for seniors, patients with chronic conditions, and people living alone.
From traditional home-based emergency systems to advanced wearable devices integrated with artificial intelligence (AI) and health monitoring features, the medical alert systems market is evolving rapidly. As the global demand for remote care solutions continues to grow, the market is expected to experience substantial expansion over the next decade.
Market Overview
The global Medical Alert Systems Market was valued at approximately USD 8 billion in 2023, and is projected to reach USD 18–20 billion by 2032, growing at a compound annual growth rate (CAGR) of around 9–11% during the forecast period.
This growth is fueled by demographic changes, rising awareness about personal health security, and the integration of smart technology with traditional emergency systems.
Download a Free Sample Report:-https://tinyurl.com/mr2kbj59
Key Drivers Fueling Market Growth
Aging Population
One of the most significant growth drivers is the increasing elderly population worldwide. According to the World Health Organization (WHO), by 2030, one in six people globally will be over the age of 60. Aging increases the risk of falls, medical emergencies, and chronic illnesses, creating high demand for reliable alert systems.
Medical alert devices allow seniors to maintain their independence at home while offering their families peace of mind.
Rising Adoption of Remote Patient Monitoring (RPM)
As healthcare shifts from hospital-centered care to home-based care, remote patient monitoring (RPM) systems have surged in popularity. Medical alert systems equipped with health tracking features, GPS, fall detection, and emergency calling capabilities are critical components of this evolving healthcare landscape.
This shift is particularly evident in post-acute care and chronic disease management.
Technological Advancements
Modern medical alert systems have moved far beyond the simple emergency button. The latest devices incorporate:
GPS-based location tracking.
Automatic fall detection.
Voice-activated emergency assistance.
Biometric monitoring (heart rate, oxygen saturation, glucose levels).
Smartwatch and smartphone integration.
AI-powered alert systems are even capable of learning user patterns and sending preemptive alerts for abnormal activities.
Increasing Healthcare Costs
With the cost of institutional elder care on the rise, medical alert systems present a cost-effective alternative. For seniors who wish to age in place, a monthly subscription to a medical alert service is significantly more affordable than nursing homes or full-time caregivers.
Market Challenges
False Alarms and Device Reliability
False alarms are one of the major challenges in the adoption of medical alert systems, especially for fall detection solutions. While sensor accuracy has improved, systems occasionally trigger false alerts due to misread movements.
This leads to user frustration and, in some cases, a decline in trust toward these solutions.
Privacy and Security Concerns
With modern medical alert systems collecting sensitive user health and location data, concerns over cybersecurity and data privacy are increasingly relevant. Manufacturers are now expected to implement robust data encryption, secure cloud storage, and GDPR or HIPAA compliance.
Initial Cost Barriers
Though the subscription cost of medical alert services is affordable, some systems require an upfront investment in hardware or setup, which can discourage adoption — especially in developing economies.
Market Segmentation
By System Type:
Landline-based Medical Alert Systems Traditional devices connected via home phone lines.
Mobile (Cellular) Medical Alert Systems Wireless devices offering nationwide coverage without reliance on a landline.
Wearable Medical Alert Devices Smartwatches, pendants, and other wearable formats equipped with emergency buttons, GPS, and fall detection.
By Technology:
Automatic Fall Detection
GPS Location Tracking
Two-way Voice Communication
Activity and Health Monitoring
By End-User:
Home-based Users
Assisted Living Facilities
Hospitals & Clinics
Nursing Homes
Emerging Trends
AI and Predictive Analytics
The fusion of AI with medical alert systems is enabling real-time risk assessment and predictive insights. These systems can learn a user’s daily routine and alert caregivers if any anomaly or deviation is detected, often before a crisis occurs.
Integration with Smart Home Ecosystems
Integration with IoT platforms and smart home devices is enhancing user experience. Devices can now interact with Amazon Alexa, Google Home, and smartwatches, offering voice-activated assistance and better accessibility.
Enhanced Wearable Design
Modern wearable medical alert devices are increasingly stylish and comfortable, addressing the stigma that older devices carried. This design evolution is making them more acceptable to younger populations with chronic illnesses and active seniors.
Shift Toward Subscription Models
A growing number of companies are adopting the as-a-service model by offering their devices free or at subsidized prices in exchange for long-term subscription contracts. This approach improves affordability and ensures steady revenue streams for vendors.
Regional Insights
North America
North America leads the market, thanks to:
A high proportion of the elderly population.
Advanced healthcare infrastructure.
Strong adoption of home-based health technologies.
Companies such as ADT Health, Philips Lifeline, Bay Alarm Medical, and Medical Guardian driving innovation.
Europe
Europe is the second-largest market, driven by:
A focus on home healthcare solutions.
Widespread digital health policies.
Increased funding for eldercare initiatives.
Countries such as Germany, France, and Scandinavia are at the forefront.
Asia-Pacific
The Asia-Pacific market is projected to grow at the fastest pace due to:
Rapidly aging populations in Japan, China, and South Korea.
Increased health awareness.
Government initiatives promoting elder care technologies.
Competitive Landscape
The Medical Alert Systems Market is moderately competitive, with both established healthcare companies and new entrants innovating continuously.
Major players include:
Philips Lifeline
ADT Health
Bay Alarm Medical
Medical Guardian
LifeStation
GreatCall (Lively)
Alert1
MobileHelp
Rescue Alert
QMedic
These companies are leveraging partnerships with healthcare providers, insurance companies, and home healthcare agencies to expand their market share.
Forecast to 2032
Looking ahead, the medical alert systems market is likely to be shaped by:
Telehealth Integration — Devices will integrate directly with virtual care platforms for real-time communication with healthcare professionals.
Next-gen AI Solutions — Predictive emergency alerting and anomaly detection.
Miniaturization and Battery Advancements — Smaller devices with longer battery life will improve comfort and convenience.
Expanded Regulatory Support — Governments worldwide are likely to recognize medical alert systems as part of national health policies, spurring adoption.
Conclusion
The medical alert systems market is poised to play a crucial role in the future of elder care, chronic disease management, and home-based healthcare. As global healthcare systems move toward prevention-focused and patient-centered care, the demand for reliable, connected, and intelligent alert solutions will continue to rise.
Driven by advances in sensor technology, AI, and cloud connectivity, medical alert systems are evolving beyond emergency buttons to become comprehensive health and safety companions for individuals across all age groups.Read Full Report:-https://www.uniprismmarketresearch.com/verticals/healthcare/medical-alert-systems
0 notes